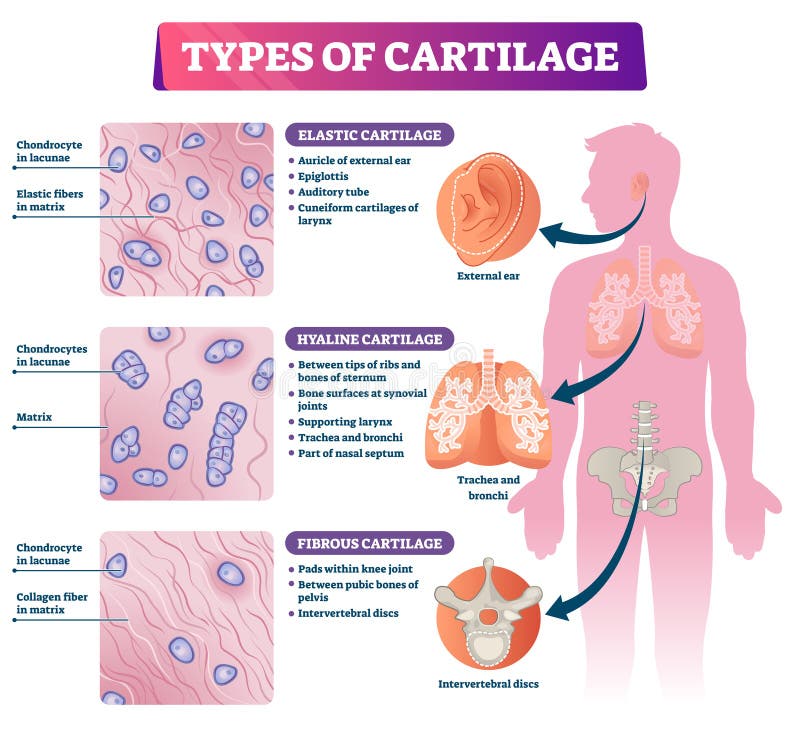
Types of Cartilage Vector Illustration. Labeled Educational Tissue Scheme. Stock Vector - Illustration of bone, cellular: 164166812

A simple padding scheme: The packets of the actual traffic (top) are... | Download Scientific Diagram
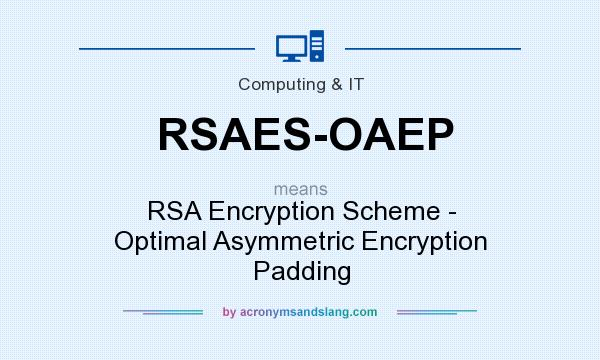
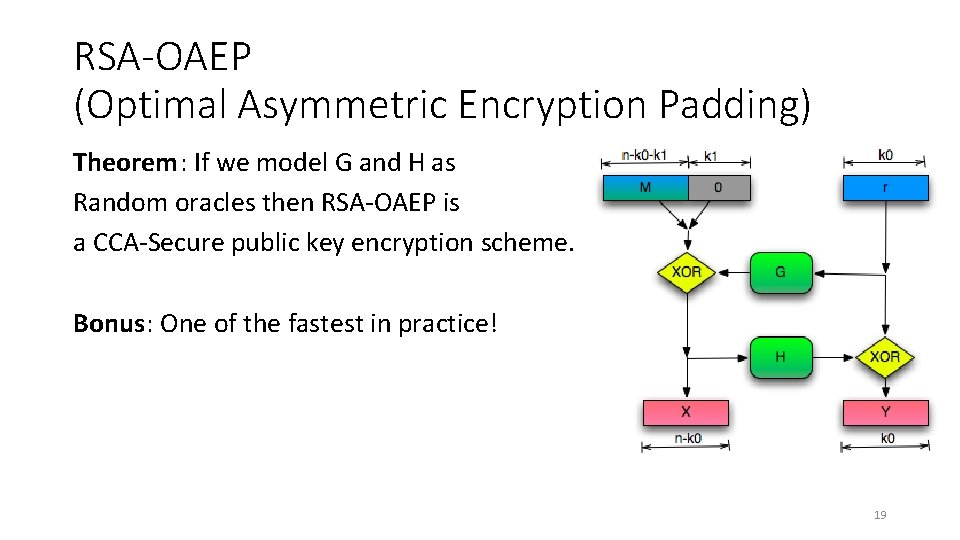
RSAES-OAEP - "RSA Encryption Scheme - Optimal Asymmetric Encryption Padding" by AcronymsAndSlang.com

Padding Oracle Attack on PKCS#1 v1.5: Can Non-standard Implementation Act as a Shelter? | springerprofessional.de

Identifying and Exploiting Padding Oracles. Brian Holyfield Gotham Digital Science - PDF Free Download
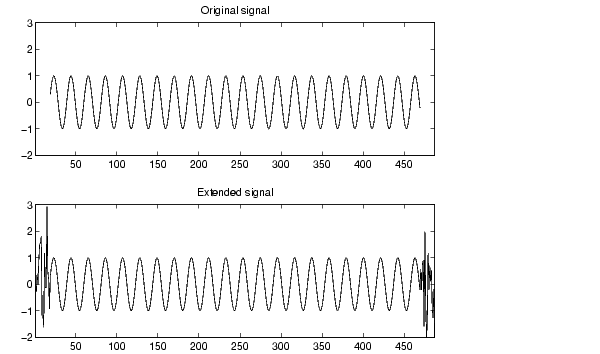
Signal Extensions: Zero-Padding, Symmetrization, and Smooth Padding :: Advanced Concepts (Wavelet Toolbox)








![Block Ciphers - Java Cryptography [Book] Block Ciphers - Java Cryptography [Book]](https://www.oreilly.com/library/view/java-cryptography/1565924029/httpatomoreillycomsourceoreillyimages2081165.png)